
Steganography - Hide zip inside an image
Today, it's steganography talk day. For those who do not know steganography is a technique for hiding content within other content.
In the past, the technique was used in pictures, letters, etc. Texts were hidden in images so that the original content could not be identified by anyone.
Steganography (from the Greek "hidden writing") is the study and use of techniques to conceal the existence of one message within another, a form of security by obscurantism. Steganography is the particular branch of cryptology that consists in having one written form camouflaged in another in order to mask its true meaning. It is important to stress the difference between cryptography and steganography. While the first conceals the meaning of the message, the second conceals the existence of the message.
To test the technique we will use any image. In this example, I will use a Mickey Mouse image, named "mickeymouse.jpg", which you can see below:

This is a normal picture without any hidden content. Now, to hide a zip file inside the image, let's do the following:
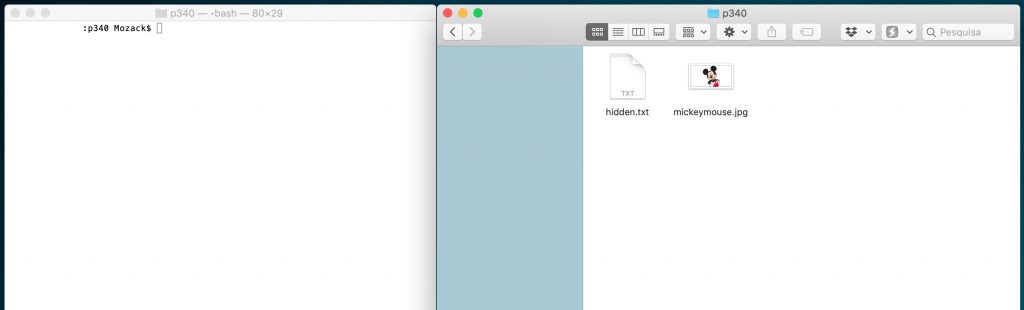
1 - Create a .txt file and write anything on it. In my case, I create a file with the name hidden.txt and put it inside: "https://danieljesus.pt/2019/03/24/esteganografia-esconder-zip-numa-imagem/". Now I have 2 files in the folder: "mickeymouse.jpg" and "hidden.txt":
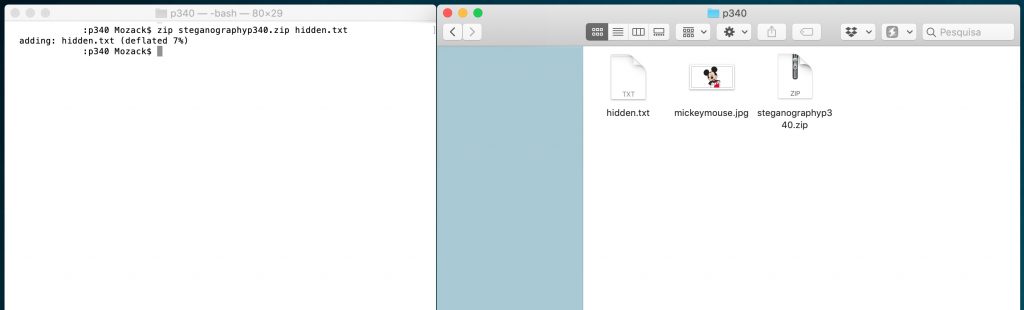
2 - By the command line, we will compress the file "hidden.txt" and we will call it "steganographyp340.zip":
- $ zip steganographyp340.zip hidden.txt
3 - Now that we have our "zipped" hidden.txt, with the name "steganographyp340.zip", we take the image "mickeymouse.jpg" and merge the files and call it "stegano_out.png". Then, from the command line, execute:
- $ cat ./mickeymouse.jpg ./steganographyp340.zip > stegano_out.png
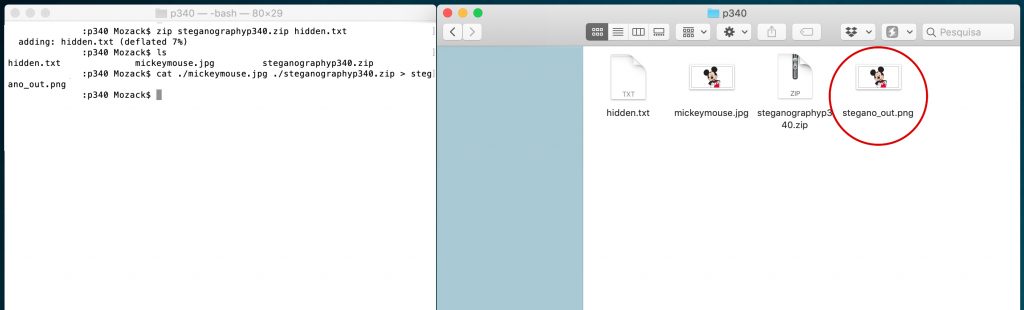
At the moment, we have our file hidden in the image stegano_out.png, which as you can see in the previous print, the PC detects as normal image ...
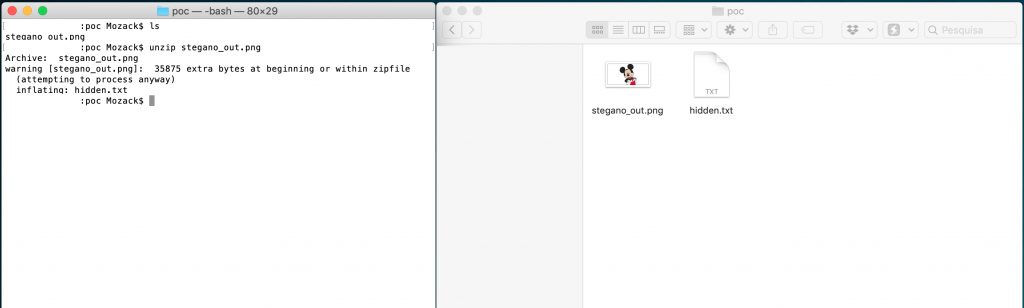
Now, in order to see the hidden content of the image, simply do the reverse process, that is, as simple as decompressing the image.
- $ unzip ./stegano_out.png
O resultado será algo assim:
Of course, if the site where they are going to upload re-creates the image in the upload, the zip file is lost in the process, however, several places do not make the image recreation process, thus keeping the hidden.zip inside.

To test the process, just save the image above and do the "unzip".
 | |
| Full Stack Developer | Security Researcher |
